TheLatestTechNews Blog
Discover fresh ideas and expert opinions from our global community of guest authors and technology enthusiasts
 Read Full Article: Streamline Your Notes with Microsoft OneNote’s AI-powered Handwriting Straightening
Read Full Article: Streamline Your Notes with Microsoft OneNote’s AI-powered Handwriting StraighteningStreamline Your Notes with Microsoft OneNote’s AI-powered Handwriting Straightening

|
The digital note-taking landscape continues to evolve, and Microsoft remains at the forefront of innovation. Microsoft OneNote, a popular choice for students, professionals, and anyone…
 Read Full Article: The Language of Data: How Scripting Transforms Raw Information into Insights
Read Full Article: The Language of Data: How Scripting Transforms Raw Information into InsightsThe Language of Data: How Scripting Transforms Raw Information into Insights

|
In today’s data-driven world, the ability to extract meaningful insights from vast amounts of information is crucial for businesses, organizations, and individuals alike. From analyzing…
 Read Full Article: Western Digital Unveils Supercharged Storage Solutions for Next-Gen Media Workflows
Read Full Article: Western Digital Unveils Supercharged Storage Solutions for Next-Gen Media WorkflowsWestern Digital Unveils Supercharged Storage Solutions for Next-Gen Media Workflows

|
Las Vegas, Nevada – April 17, 2024 – Western Digital Corp. (NASDAQ: WDC) closed the curtain on a groundbreaking showcase of next-generation storage solutions designed…
 Read Full Article: Exploring Online vs. In-Person Full Stack Development Courses: Pros and Cons
Read Full Article: Exploring Online vs. In-Person Full Stack Development Courses: Pros and ConsExploring Online vs. In-Person Full Stack Development Courses: Pros and Cons

|
Deciding between online and in-person Full Stack Development courses can be tricky! This guide explores the pros and cons of each option, including flexibility, cost,…
 Read Full Article: Unleash Your Inner Electronics Expert with the ZOYI 703S 3-in-1 Oscilloscope Multimeter Generator
Read Full Article: Unleash Your Inner Electronics Expert with the ZOYI 703S 3-in-1 Oscilloscope Multimeter GeneratorUnleash Your Inner Electronics Expert with the ZOYI 703S 3-in-1 Oscilloscope Multimeter Generator

|
Introducing the ZOYI 703S, a powerful and versatile 3-in-1 device that combines the functionality of an oscilloscope, multimeter, and signal generator – all in one…
 Read Full Article: How to Use an Age Verification System in Your Business?
Read Full Article: How to Use an Age Verification System in Your Business?How to Use an Age Verification System in Your Business?

|
Businesses use age verification systems to confirm the age of individuals accessing age-restricted products or services. It includes alcohol, tobacco, gambling, adult content, or specific…
 Read Full Article: Everything You Should Consider Before Selling Your Device
Read Full Article: Everything You Should Consider Before Selling Your DeviceEverything You Should Consider Before Selling Your Device

|
Technology is changing faster than expected. The latest gadget models are being released constantly and come with new, exciting functions and features. However, some people…
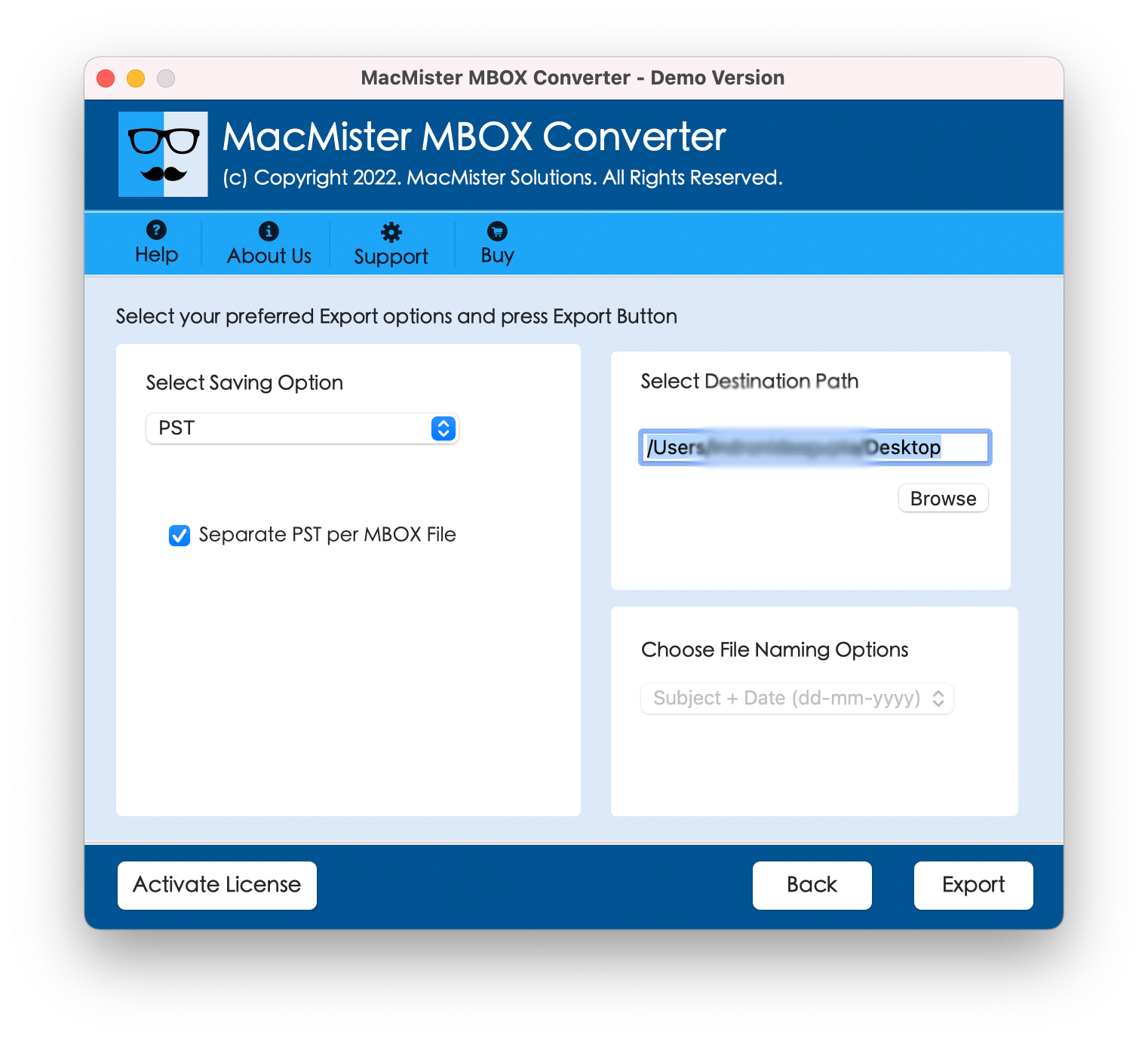
 Read Full Article: How to See MBOX File of Apple Mail in Windows Outlook?
Read Full Article: How to See MBOX File of Apple Mail in Windows Outlook?How to See MBOX File of Apple Mail in Windows Outlook?

|
Have you recently moved to Windows from a Mac system and shifted to critical MBOX files? Need to urgently transfer them to Windows Outlook? Wondering…
 Read Full Article: Biometrics in Cyber Security: The Future of Secure Access?
Read Full Article: Biometrics in Cyber Security: The Future of Secure Access?Biometrics in Cyber Security: The Future of Secure Access?

|
In today’s increasingly digital world, cybersecurity has become paramount. Protecting our data, identities, and online assets is crucial, and traditional methods like passwords are becoming…
 Read Full Article: JEYI i9X Smart Display M.2 Dual Protocol SSD Enclosure: A Budget-Friendly Option?
Read Full Article: JEYI i9X Smart Display M.2 Dual Protocol SSD Enclosure: A Budget-Friendly Option?JEYI i9X Smart Display M.2 Dual Protocol SSD Enclosure: A Budget-Friendly Option?

|
Thinking of giving your computer a storage boost? The JEYI i9X Smart Display M.2 Dual Protocol SSD Enclosure from Banggood promises an easy way to…
 Read Full Article: Evaluating the ROI for Business Fibre Broadband and Leased Line Connection
Read Full Article: Evaluating the ROI for Business Fibre Broadband and Leased Line ConnectionEvaluating the ROI for Business Fibre Broadband and Leased Line Connection

|
In the modern digital world, businesses of all sizes require a fast, dependable internet connection to operate properly. To maintain productivity and efficiency at the…
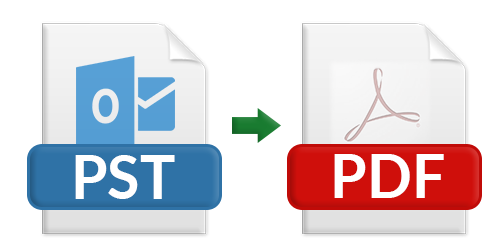
 Read Full Article: Top Methods for Convert Outlook PST Files in Bulk to PDF
Read Full Article: Top Methods for Convert Outlook PST Files in Bulk to PDFTop Methods for Convert Outlook PST Files in Bulk to PDF

|
This article describes a flawless method by which an individual can effortlessly convert multiple PST files to PDF.